There are few good reason to the last minute and not being prepared, mainly because I was invited late on the event and I had to prepare my environment as well, when others had their tools ready.
So I was late in the party. As most of the events for me, can only take place after working hours, I had to be quick in order to catch up with the others.
The event, roughly 500 hosts in different networks (results from nmap scan were provided) non sequential and in different networks waiting to be scanned.
On the last months my favorite tool for web enumeration had been ffuf, https://github.com/ffuf/ffuf, but even with that alone I couldn't catch up easily on the others.
Web dirbuster tool comparison
Some stats first on ffuf and comparison with other tools used in web 'dir-busting'
I'll be using http://testphp.vulnweb.com/ for the tests and default as much as possible, parameters on each tool.
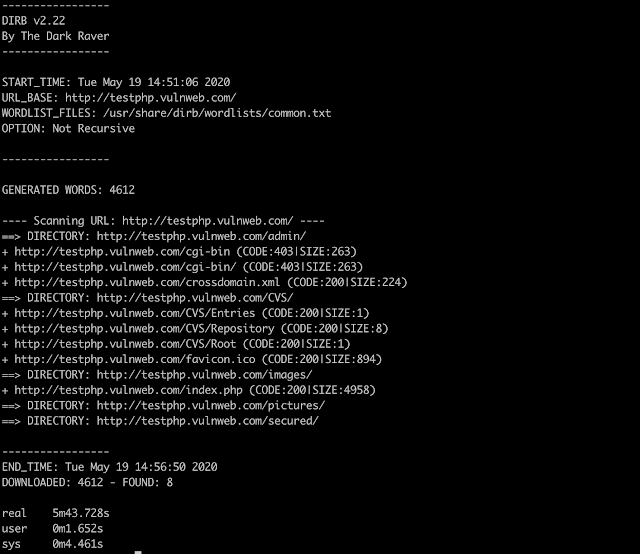
dirb, time 5.43 minutes.
Image 1. dirb
gobuster time 8.8 seconds
Image 2. gobuster
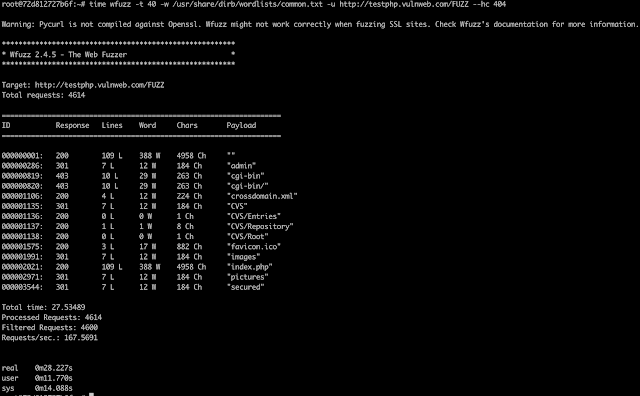
wfuzz time 28.2 seconds
Image 3. wfuzz
fuff time 8.7 seconds
Image 4. ffuf
Turbo intruder time 13.3 seconds.
Image 4. Turbo intruder
Brief comparison, lower is better:
Image 5. Brief comparison
So if you are not using ffuf, or turbo intruder ( I will explain later in another post as to why ) I'll advise to give them a try.
Back to the methodology.
As mentioned above the data set was large and I was late. So this was my methodology to gain some advantage in time.
1. Enumeration of all common ports using aquatone, eg:
cat hosts | aquatone -ports large -out aquatone
2. Use gnu parallel to feed ffuf workers with the urls from aqutatone, verified working, using:
cat aquatone/aquatone_urls.txt | parallel -j 50 -I{} ffuf -w /usr/share/dirb/common.txt:FUZZ -u {}FUZZ -o {#}_results.html -mc 200,403 -sf -fs 0 -of html
Aquatone is taking roughly 6 minutes for 100 hosts and it will clean up ports that are not responding.
Image 6. Aquatone results.
Ffuf was able to produce results on the first few minutes which where easy to be analysed.
The parameters on the filtering at ffuf may vary during the stage of the analysis that you are. I will recommend to have at least 403 and 301 with the 200 (OK, found) so you can see what is denied and what is redirected initially.
Having in mind that I was aiming for speed mainly and not for quality at this phase. I was able to get a good understanding on the targets and their setup in short time.
Following post will be on turbo intruder and what makes a difference on this scanner.